2016 HIPAA cases offer insights into HIPAA audits
Sample HIPAA cases
By Diane Evans
Publisher, MyHIPAA Guide
With the onset of federally mandated enforcement of patient privacy laws, it’s a good time to review lessons from HIPAA cases announced in 2016. Common themes clearly prevail.
In reviewing these lessons, keep in mind that the feds continue to clarify the stricter rules in place since 2013 under the Health Information Portability and Accountability Act (HIPAA). Since federal audits began only last year, gray areas continue to muddle the ever murky waters.
Here are some overriding messages from federal cases and news releases last year:
1. Risk Assessment:
Make this a top priority, and include all remote facilities in your assessment. Also account for the security of mobile devices and databases in the homes and cars of employees, including telecommuters. Multiple settlements drive home this point. Remember, too, that you need proper policies and procedures in place as part of risk analysis and mitigation.
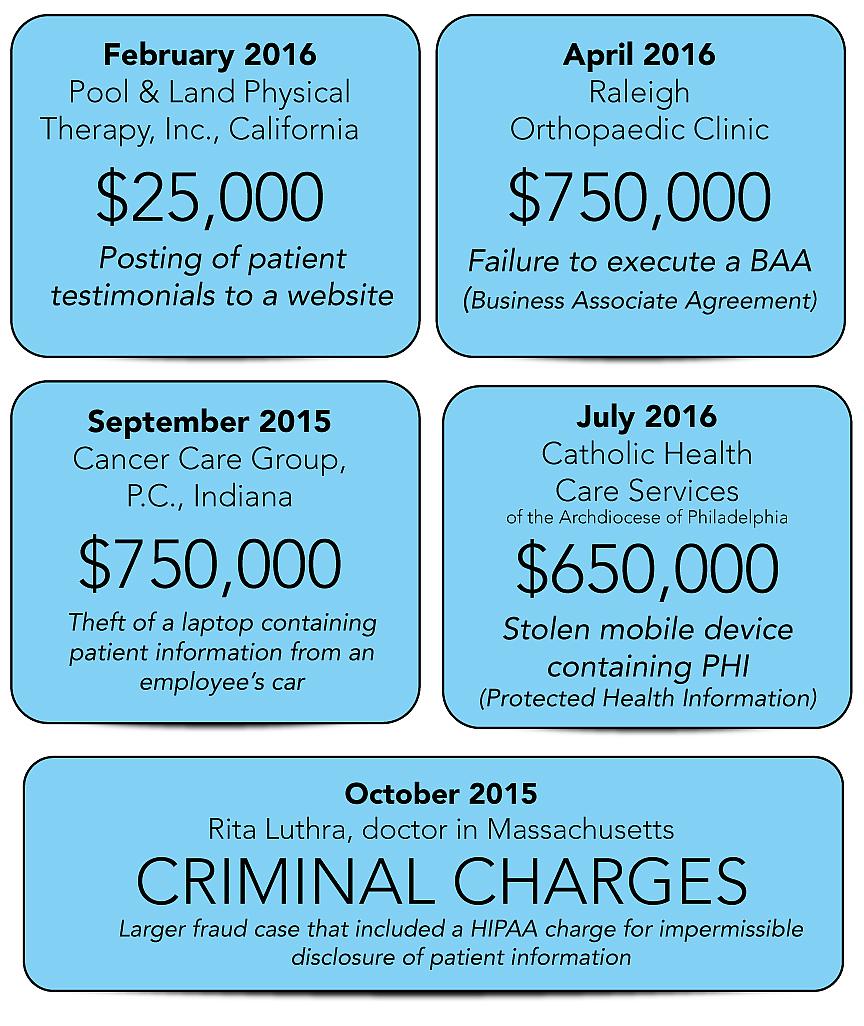
Example: The case of St. Joseph Health (SJH), which operates hospitals, home health agencies, hospice care, outpatient services, skilled nursing facilities, community clinics and physician organizations in California, Texas and New Mexico. SJH agreed to pay $2.14 million in a settlement with the U.S. Office for Civil Rights (OCR), relating to a report that files containing electronic protected health information (ePHI) became publicly accessible through internet search engines from 2011 until 2012. A server SJH purchased included a file sharing application, and the default setting allowed anyone with an internet connection to access the data, potentially breaching the privacy of nearly 32,000 patients.
The feds said: Although SJH hired a number of contractors to assess risks and vulnerabilities, evidence indicated a “patchwork” approach falling short of “enterprise-wide risk analysis.”
2. Business Association Agreements:
Again, multiple cases reinforce this as a big priority. The point is that if any outside person or vendor can potentially access private information about your patients, then you need to hold those vendors or individuals to the same rules that apply to you. You need formal agreements with them. Also know that HIPAA audits extend to business associates.
Example: The Archdiocese of Philadelphia agreed to pay $650,000 to settle potential privacy violations relating to the theft of a mobile device containing protected health information for 412 nursing home residents. In this case, Catholic Health Care Services (CHCS), an agency of the Diocese, performed IT services as a business associate to six skilled nursing facilities. The potential breach happened as a result of a theft of a CHCS-issued employee iPhone, which was unencrypted and not password protected. The information on the iPhone included social security numbers, information about diagnoses, medications and treatments, and names of family members and legal guardians.
The feds said: CHCS had no policies addressing the removal of mobile devices containing patient information from its facility, and no risk analysis or risk management plan.
Click here to read more about what happened.
3. Smaller providers:
You’re on hook, too, as HIPAA-covered providers of all types and sizes are subject to audits. Last fall, OCR announced it is now working with its regional offices to “more widely investigate the root causes of breaches affecting fewer than 500 individuals.” The regional offices will still have discretion on which smaller breaches to investigate, but each office will increase its efforts to address these smaller breaches.
4. Insider threats:
In a recent newsletter, OCR discussed the “insider threat” as one of the largest threats to the security of patient information within organizations. The agency noted that even some cyberattacks may be insider-driven.
According to a recent survey, conducted by Accenture and HfS Research, 69% of organizations surveyed reported experiences with malicious activity on the part of insiders, including current or former employees, contractors and business associates.
Keep in mind, whenever patient information reaches unauthorized ears and eyes, nothing stops it from getting on social media. And yes, that does happen, especially among patients who are most vulnerable and unsuspecting.
Questions? Contact Diane Evans, Publisher of MyHIPAA Guide, at devans@medmediamart.com.
Disclaimer: This content is for informational purposes only. It is not is not intended as a complete record of compliance-related changes and announcements, nor should it be construed in any way as legal advice.
